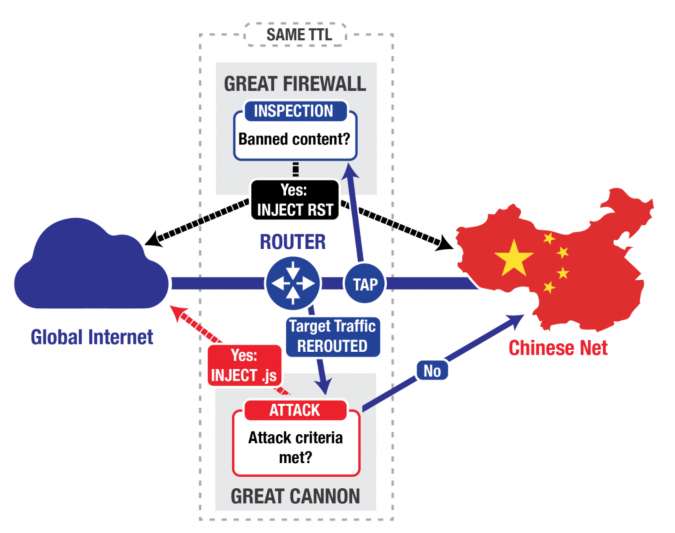
Simplified logical topology of the Great Cannon and Great Firewall | image from
Citizen Lab at the University of Toronto’s Munk School of Global Affairs
The Chinese government appears to have used distributed denial-of-service attacks against a nonprofit organization, GreatFire.org, that helps Chinese users circumvent the administration’s Internet censorship regime, according to a report by the Citizen Lab at the University of Toronto’s Munk School of Global Affairs that ICSI researchers collaborated on. While the Chinese administration has long censored the Internet by using a tool known as the Great Firewall to block traffic to certain web sites, the new system works offensively by redirecting traffic to attack targets.
The researchers say that the tool, which they have named the Great Cannon, was responsible for a flood of Internet traffic on March 16 that nearly crashed servers rented from Amazon Web Services by GreatFire to provide mirror images of blocked sites. On March 26, a similar attack was directed at GitHub pages run by GreatFire.org. At its height, the attack was racking up $30,000 a day in bandwidth fees from Amazon, according to GreatFire's blog. GitHub called the attack on its repositories the largest distributed denial of service attack in its history.
In the report, released April 10, the researchers said there are similarities between the the Great Cannon and the Great Firewall, including where they are located in the network topology relative to the researchers’ machines.
But the Great Cannon differs significantly as well. For one, it is an offensive tool that targets traffic from outside the county. When users outside China send requests to certain servers inside it, the Great Cannon injects malicious code that hijacks their browsers, recruiting them to send requests to the attack target.
"This is very much an escalation," said Bill Marczak, a student in the Networking and Security Group and a research fellow of the Citizen Lab, in an interview with the Washington Post.
The Great Cannon also appears to target traffic to specific IP addresses. In the March attacks, it intercepted a small portion of traffic sent to servers run by Baidu, the country’s largest search engine and most popular web site. It also intercepted traffic for web sites that used Baidu’s analytics or displayed ads served by Baidu’s network.
While only a small percentage of the traffic to Baidu was weaponized, the researchers stress that with some simple adjustments, the tool could target not only traffic sent to specific IP addresses but also traffic sent from specific IP addresses to Chinese servers.
The report is by Bill Marczak, Nicholas Weaver, David Fifield, and Vern Paxson of Networking and Security; Roya Ensafi, a former Networking and Security researcher who is now at Princeton University; and their colleagues from Citizen Lab, Jakub Dalek, Sarah McKune, Arn Rey, John Scott-Railton, and Ronald Deibert.
Selected Media Coverage (full coverage is available on our press page):
"Don’t Be Fodder for China’s ‘Great Cannon,’" April 10, 2015, Brian Krebs, Krebs on Security

